ProtectWorks AntiVirus detects both Mac and non-Mac viruses, trojans, worms and spyware. Below is a brief description of just some of the Mac-specific malware that has appeared on OS X.
Amphimix : MP3Concept
Discovered 9 April 2004
Description
This is a proof of concept Trojan horse that contains an MP3 file with an embedded application; the file will appear to be a normal MP3 file.
If you run the application it will display the following message in a dialog box, "Yep, this is an application (So what is your iTunes playing right now?)" and iTunes will launch and play the MP3 file of a man laughing wildly.
Hovdy.A : AplS.Saprilt.A
Discovered 20 June 2008
Description
Hovdy.A is a Trojan horse that exploits a vulnerability in Apple's Remote Desktop Agent that could allow software to perform commands with root access.
The Trojan attempts to install a number of files throughout your Mac in various locations, as well modifying the startup and login sequence so that it always runs. It lowers security by manipulating the firewall and setting up several remote access and network features, in addition, it will try to gather local account information and forward this to the attacker.
DNSChanger : OSX.RSPlug.A
Discovered 31 October 2007
Description
This is a Trojan horse pretending to be a codec that allows users to view pornographic videos. The Trojan modifies the DNS settings on the compromised computer to unwittingly redirect users to other potentially malicious websites.
It also sends the Mac's CPU type, User Identifier (UID), and the hostname to the following URL:
http://85.255.121.37
Fromr.A : AS.MW2004
Discovered 14 May 2004
Description
This threat is an Applescript Trojan posing as a Microsoft Word 2004 Installer that attempts to delete the user's home folder and all of its contents. It is displayed with a custom psuedo-Microsoft installer icon.
Note: If the user is logged in as root then the entire home folder and all of its contents will be deleted. If the user is not logged in as root then a Permission Denied error will appear but many of the files and folders will still be deleted from the home folder.
Leap.A
Description
Leap.A is a virus/worm that spreads via iChat by forwarding a file named "latestpics.gz" to everyone in your Buddy List.
Once the archive file is expanded and the JPEG image file double-clicked the virus writes itself to disk. It installs a file called apphook.bundle in either the user's InputManagers folder or /Library/InputManagers folder (depending if you're logged in as root). Apphook.bundle attempts to send latestpics.gz to everyone in your iChat's Buddy List.
The virus also uses Spotlight to search for the four most recently used applications and infects them with a copy of itself. However, due to a bug in the virus the infection may corrupt the application, preventing it from ever being launched.
On Intel Macs the Trojan will infect applications but not spread via iChat.
InqTana
Description
InqTana is a proof-of-concept worm that spreads via a vulnerability in Apple's Bluetooth technology.
Users must accept a file transfer to receive the worm (3 files) and get infected in the first place, but then the worm exploits a BlueTooth vulnerability by traversing the directory structure and copying itself in a directory outside the normal exchange path which allows the worm to become active the next time the Mac is restarted. After restart the worm searches for Bluetooth devices to 'push' its three files to.
Note: The worm is using a demo version of a commercial Bluetooth software library, which is time limited, so may not replicate.
The Bluetooth vulnerability was fixed in Apple Security Update 2005-006
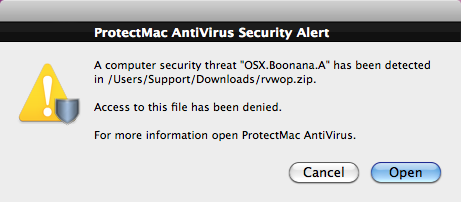
OSX.Boonana : Trojan.Java.Boonana, OSX.Koobface
Discovered 1 November 2010
A version of the Koobface trojan has been discovered on social networking sites, Facebook, Twitter and Myspace, as well as on popular internet sites, which has the ability to infect Mac computers.
Adopting 'social engineering' techniques to catch out the unwary. TheTrojan tries to persuade users on social networks to click on a link to see a video of themselves. In other cases the Trojan has been discovered masquerading as 'interesting' videos on the internet.
The multi-platform Java threat is designed to run not only on Mac OS X, but Windows and Linux, too. In all cases so far on Mac a Java security alert appears requesting access to your computer and the the digital signature of the applet could not be verified.
***Selecting Deny will prevent the threat from running!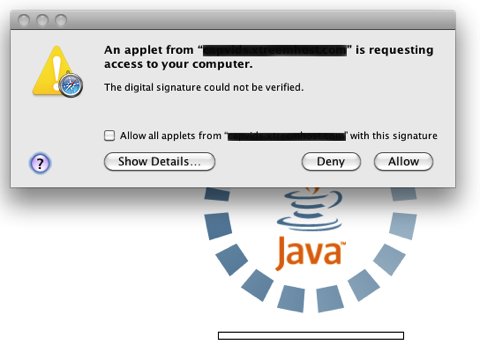
If further proof were required to raise suspicions then clicking on the Show Details button will display information of an untrusted certificate associated with the applet.
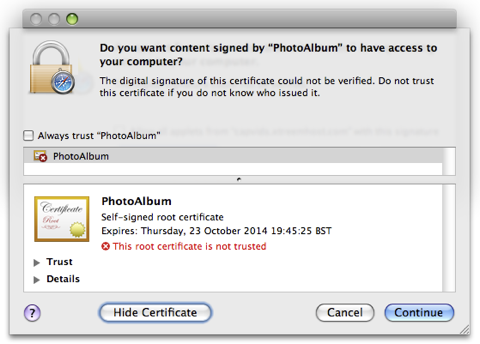
If a user is persuaded to authorize the Java applet, it has the potential allow remote access to the users's computer, setup the computer as a host server to send spam and spread the trojan, and contact a number of remote sites with the intent of downloading further malicious software.
An installer run on a computer will create a hidden folder in the user's Home folder called .jnana, and will modify the startup items of the computer to allow the threat to run automatically on each restart.
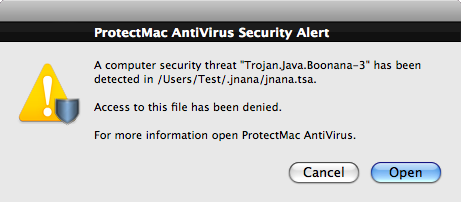
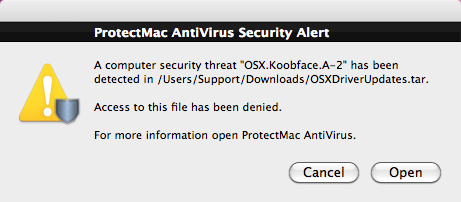
We obviously recommend that users do not click on any speculative link they come across on their social network account and be highly suspicious of any installer window they have not initiated.
Should you see unverified software requiring access to your computer, deny it!!
OSX.DevilRobber : OSX/Miner
Discovered 31 Oct 2011
Description
A Trojan distributed on BitTorrent file-sharing websites inside copies of popular Mac OS X applications, such as GraphicConverter, Flux and CorelPainter.
The Trojan harvests personal details from your Mac, usernames and passwords, as well as third-party encryption software information and Safari browsing history, and attempts to send these details to a remote server.
The Trojan also steals a user's bitcoin wallet, if present, and hijacks the Graphic Processing Unit (GPU) on their Mac to perform calculations to 'mine' bitcoins. Users, therefore, may notice a sluggishness as their computer resources are utilized in the background.
If the parent application is installed then the Trojan will create a folder in your user area ~/Library/mdsa1331/ and a plist file in ~/Library/LaunchAgents/ called com.apple.legion.plist to ensure that it runs each time on startup.
Note, the Trojan will not install itself if the network analzing tool, Little Snitch, is installed.
*Bitcoins is an alternate digital currency system that allows users to pay for (limited) goods and services online. Users can transfer bitcoins anonymously through peer-to-peer digitally signed transactions. Bitcoins can also be converted into more recognizable currencies through a small number of specialized broker sites.
OSX.iMuler-1
Description
This is a backdoor Trojan that would allow a hacker remote access to your computer should it run.
The backdoor Trojan is downloaded by a 'dropper' Trojan posing as a PDF document (OSX.Revir-1), which connects to a remote server to download this threat.
OSX.iWorkServices.A
Discovered 22 January 2009
Description
This is a Trojan Horse that is packaged with pirated copies of Apple's iWork 09 on BitTorrent websites. The BitTorrent file is approximately 450Mb in size and when downloaded contains a folder named iWork.09, with a zip file, iWork09.zip, and a text file with a product serial number, serial.txt.
The zip file contains a valid copy of iWork 09 as well as the Trojan Horse. Expanding the zip file and running the iWork 09 installer meta-package installs not only iWork 09 but also the Trojan.

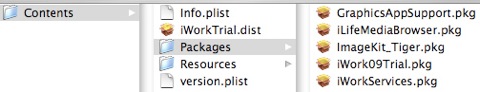
The iWorksServices installer package is contained within the Contents folder and installs the Trojan in /usr/bin/iWorkServices with corresponding files in /System/Library/StartupItems/iWorkServices. The Trojan attempts to connect to a remote server over the internet during installation, allowing it to broadcast its existence and possibly download further malware. The files in StartupItems ensure that the Trojan is run each time you restart your Mac.
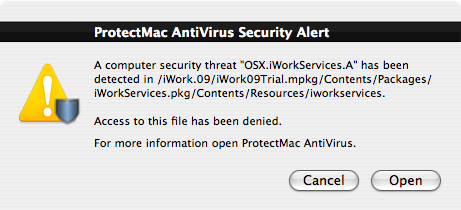
ProtectMac AntiVirus Alert of the installer package
Removal
If the Trojan has been installed on your Mac, it should be deleted from the /usr/bin folder and both the 'iWorkServices' and the 'iworkservices' root processes killed or your Mac restarted. The folders /System/Library/StartupItems/iWorkServices and /Library/Receipts/iWorkServices.pkg should also be removed.
OSX.iServices.B
Discovered 26 January 2009
Description
This is a Trojan Horse that is packaged with pirated copies of Adobe PhotoShop CS4 on BitTorrent websites.
The zip file contains a commercial version of Adobe PhotoShop CS4 as well as an application to 'crack' the software's serial number protection. Running the Crack application installs the Trojan on your Mac.
The Trojan is written to /usr/bin/DivX and also to /private/var/tmp but given a random filename, such as tmp.0.ORbnHw. Associated files are also written in /System/Library/StartupItems/DivX to ensure that the Trojan runs each time on Startup. The Trojan attempts to connect to a remote server, freehostia.com:1024, over the internet, allowing it to broadcast its existence and download further malware.
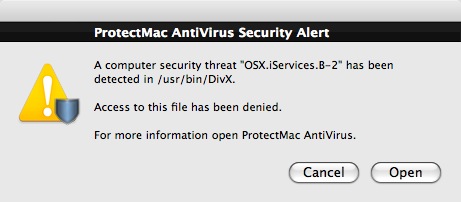
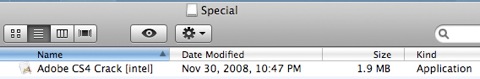
ProtectMac AntiVirus Alert of the Crack application
Removal
If the Trojan has been installed on your Mac, it should be deleted from the /usr/bin folder and the /private/var/tmp folder, the 'DivX' root processes killed or your Mac restarted. The folder /System/Library/StartupItems/Divx should also be removed.
OSX.Jahlav.A : OSX.RSPlug.D
Discovered 23 November 2008
Description
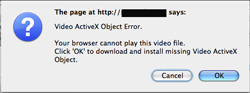
This Trojan comes from the same virus writing group that produced the RSPlug.A/ DNSChanger Trojan. It can be found on pornographic websites and purports to be a fix for Active X errors when attempting to view online videos. Once the user sees these alerts the only way to terminate the dialog sequence and prevent the Trojan from being downloaded is to quit the browser.
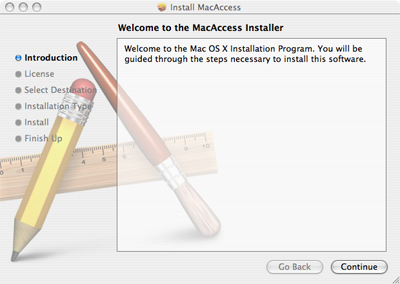
The Trojan is delivered to the user's Mac as a disk image (dmg file) and mounts an installer package on the desktop called "install.pkg". When the installer package is double-clicked an Installer titled "MacAccess" is run.
This Trojan differs from RSPlug.A in that it includes several scripts that communicate with remote servers, sending computer information such as OS version, IP address and processor type, as well as downloading malicious software (malware) to the user's Mac.
OSX.Jahlav.B : OSX.RSPlug.E
Discovered 2 December 2008
Description
This is a variant of the OSX.Jahlav.A/RSPLug.D Trojan. It can be found on pornographic websites and purports to be a fix for Active X errors when attempting to view online videos. Once the user sees these alerts the only way to terminate the dialog sequence and prevent the Trojan from being downloaded is to quit the browser.

The Trojan is delivered to the user's Mac as a disk image (dmg file) and mounts an installer package on the desktop called "install.pkg". When the installer package is double-clicked an Installer titled "MacAccess" is run.

This Trojan includes several scripts that communicate with remote servers, sending computer information such as OS version, IP address and processor type, as well as downloading malicious software (malware) to the user's Mac.
OSX.Jahlav.C : OSX/Jahlav-C, OSX.RSPlug.C and OSX.RSPlug.K
Discovered 11 June 2009
Description
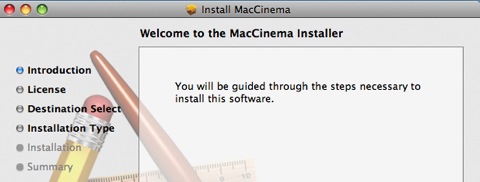
This Trojan is a variant of the Jahlav family of Trojans, it purports to be an installer for a missing Video ActiveX Object.
The Trojan is delivered to the user's Mac as a disk image (dmg file) and mounts an installer package on the desktop called "install.pkg". When the installer package is double-clicked an Installer titled "MacCinema" is run.
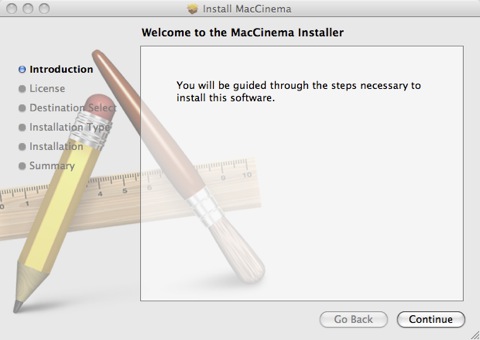
A shell script named AdobeFlash is copied to /Library/Internet Plug-Ins as part of the installation process and is configured to periodically access remote servers on the internet via a worker script, which could potentially download malicious code.
OSX.Lamzev.A : Troj/RKOSX-A : OSX.TrojanKit/Malez
Discovered 17 November 2008
Description
This is a Trojan horse that is capable of opening up a backdoor on a compromised Mac.
If the Trojan is executed it creates a file called ezmal in /Applications. A chosen host application is copied to /Application/
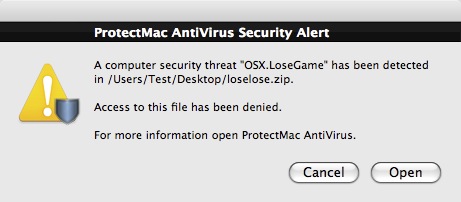
OSX.LoseGame : OSX.Loosemaque
Discovered 4 Nov 2009
Description
An arcade-style, shoot'm up alien game for Mac OS X.
When the game is run it will create 'aliens' based on the files it finds on your disk, and every time you kill an alien the associated file is deleted!
At the moment you need to go the author's website and download the game to come across it, ignoring the big red warning....
KILLING ALIENS IN LOSE/LOSE WILL DELETE FILES ON YOUR HARD DRIVE PERMANANTLY
And the warning in the Introduction....
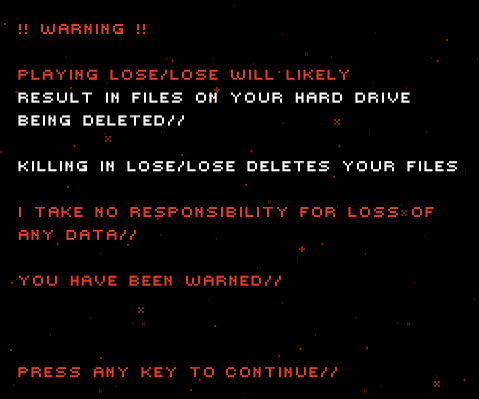
ProtectMac AntiVirus will report the game as OSX.LoseGame...
OSX.MacDefender.A : Trojan.OSX.MacDefender, MacSecurity, MacProtector, MacGuard
Discovered 3 May 2011
Description
A fake Mac antivirus product likely to be found on compromised websites when users search for key topics and images via popular internet search engines.
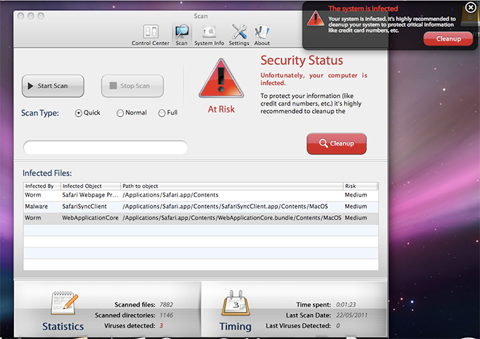
A compromised website contains JavaScript code that executes and displays a Windows-style scan of your computer.
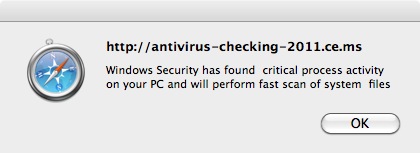
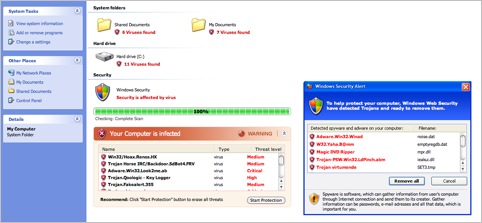
After closing the alert a zip file named, BestMacAntiVirus2011.mpkg.zip is downloaded, which extracts a Mac Installer meta-package called MacDefender.mpkg. Later variants of this threat are named Mac Security, Mac Protector, Apple Web security and Mac Guard (see also Trojan-Downloader.OSX.Fav.A).
The software runs for a short while giving the appearance that it is performing a scan of your computer.
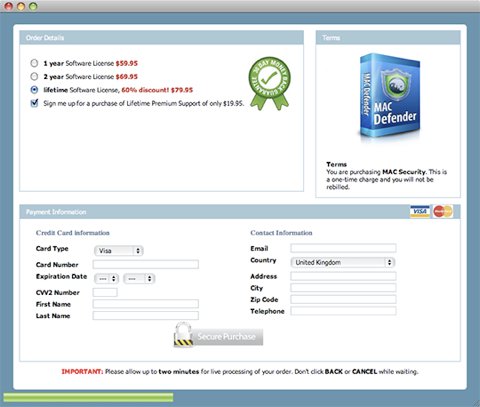
It requests that you enter your credit card details to register the product and enable the virus removal features.
Later variants portray what looks like an Apple-desktop scanning window within your web browser. A download of an Installer meta package happens automatically, downloading a file called MacSecurity.mpkg
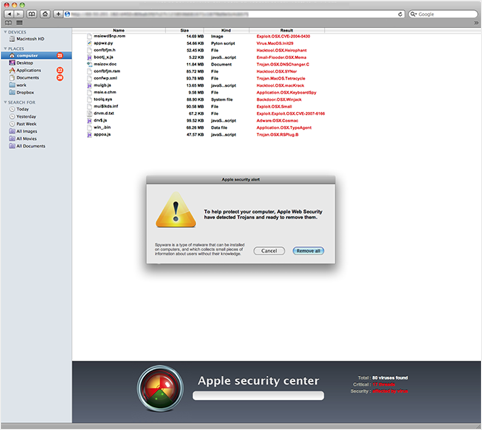
Note: The MacGuard and MacShield variants first download and run an intermediate file (trojan downloader) that does not require admin rights.
After removing the trojan with ProtectMac AntiVirus restart your computer .
How to manually removal MacDefender and any variants
Manual removal instructions
OSX.MusMinum
In its current state the threat is quite basic and even warns you in flawed English if you become infected. Furthermore, if the threat is running then it is displayed in the list of processes as "BlackHole" and can often appear on disk in a folder of the same name.
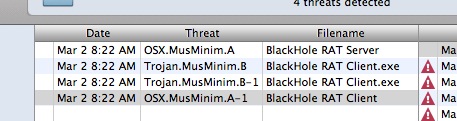
The trojan should pose little risk to Mac users at present, but we are continuing to monitor the situation closely as all indications are that the author is developing a more sophisticated variant.
As the threat is likely to appear as some kind of trojan on the internet, our recommendations as always is to be vigilant when downloading any application from the internet and only visit well-known reputable sites.
OSX.OpinionSpy
Discovered 2 June 2010
Description
Premier Opinion is a trojan application that is included with several free screensavers and video plugins. The software gets installed as part of the host application's installation, during which time you are prompted to accept the software terms of the additional software based on the understanding that you are participating in market research by providing details of your computer usage and online habits.
There’s no opt-out choice for this component during the installation phase, so if you don't want to participate in the market survey then you cannot install the screensaver in the example below.
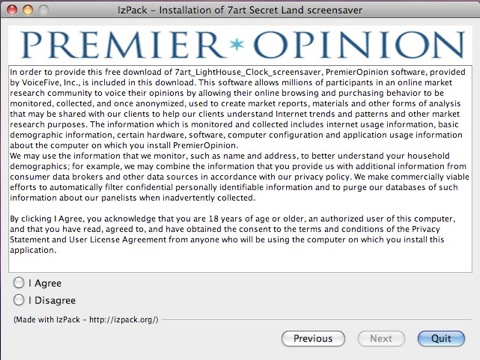
Currently it is quite easy to detect whether you have Premier Opinion installed on your computer, there's a menu bar icon at the top of your screen and most of the software is located in the Applications folder within a sub folder called Premier Opinion. 
There is also a root process called PremierOpinion (note, no space in the middle) running on your Mac, which is the main component collecting data on your computer and forwarding it across the internet - there’s also a plist file in /Library/LaunchDaemons to ensure that the root process is run on startup.
To remove the software firstly disconnect your computer from the internet and run the uninstaller located in the /Applications/Premier Opinion folder, uninstalling the host screensaver or codec in itself does not remove the Premier Opinion software.
OSX.Revir-1
Description
Is a malicious application that poses as a PDF file and attempts to disguise itself from the user when run by opening an embedded Chinese PDF document.
Meanwhile the threat will be connecting to a remote server and downloading a backdoor Trojan (MacOSX.iMuler-1), which will allow a hacker to gain remote access to your Apple computer.
OSX.RSPlug.F : OSX.RSPlug.G
Discovered 20 March 2009
Description
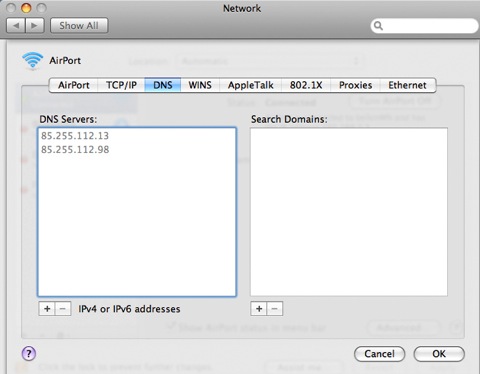
This Trojan is a variant of the DNSChanger/RSPlug Trojan that modifies your network settings, changing DNS server configuration and causing the user to be redirected to malicious websites when browsing the internet.
The Trojan has been posted to various websites claiming to be an installer for Avid Express Pro, although the title in the Installer window when run pertains to MacCinema application.
When the Installer is run the Trojan will be installed along with a cronjob to ensure that the Trojan (/Library/Internet Plug-ins/AdobeFlash) is run at regular intervals.
The modified DNS Server settings will typically have entries associated with the domain 85.255.112
OSX.Tored.A
Discovered 5 May 2009
Description
OSX.Tored.A is a proof-of-concept worm created with RealBasic that attempts to set itself up as a Botnet on infected Macs. It also tries to gather email addresses from your Address Book to propagate to other users.
Errors in the worm's code and mistakes in the email content make it very unlikely that this threat would spread even if it was 'in the wild', so this version poses a very low risk.
OSX.Tored: OSX/Tored-Fam
Discovered 10 June 2009
Description
OSX.Tored is a worm created with RealBasic that attempts to set itself up as a Botnet on infected Macs. It also tries to gather email addresses from your Address Book to propagate to other users.
Macarena
Description
Is a proof of concept virus that infects files in the current folder when they are executed.
Renepo : Opener
Discovered 25 Oct 2004
Description
Renepo is shell script virus that will make various changes to your system, including attempting to disable your firewall, download hacking tools and try and collect data from a compromised Mac.
There are no reports of this virus ever being discovered in the wild.
Sub7
This is a Mac OS X client of the Sub7 Trojan that allows backdoor remote access.
UnderHand : Cowhand
This is a backdoor trojan that can be used to remotely control a machine.
Trojan-Downloader.OSX.Fav.A
Description
This is a Mac downloader application designed to download and install a variant of the MacDefender trojan called either MacGuard or MacShield.
Whilst browsing a compromised website users will see what appears to be a scan of their computer occurring within their web browser.
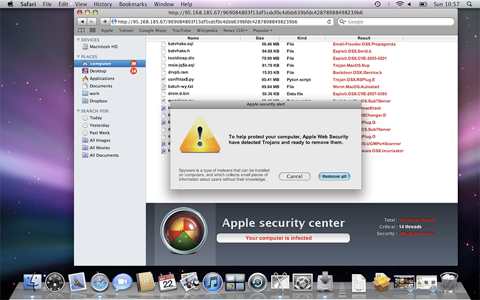
The JavaScript on the website first downloads a small zip file, anti-malware.zip, which unpacks an application called avRunner or mdDownloader. The malicious app then downloads a MacDefender trojan and installs it in the Applications folder.
An entry is also added the user's Login Items in System preferences so that the Trojan runs each time on startup.
See OSX.MacDefender for further information on this family of threats.
How to manually remove MacDefender and any variants
Manual removal instructions
Trojan.Flashback
Discovered 27 Sept 2011
Description
A backdoor Trojan threat that pretends to be an Adobe Flash Player plugin. If the backdoor Trojan runs on your computer it has the potential for remote hackers to control your Mac and retrieve sensitive information.